
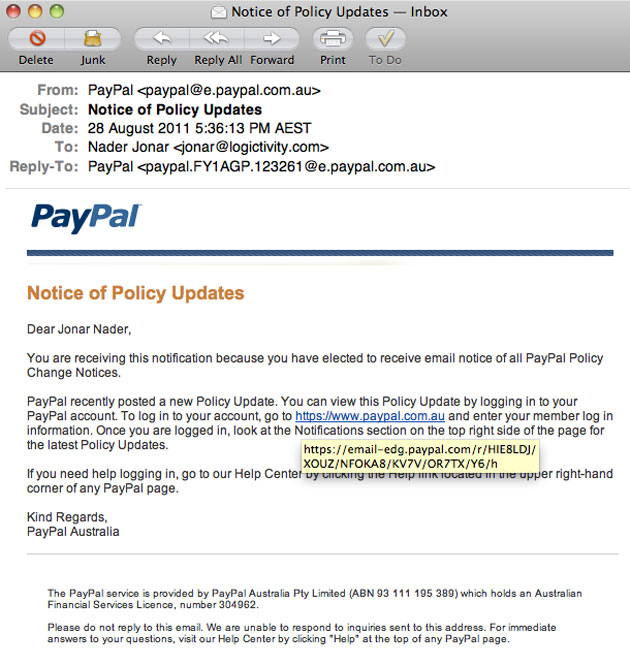
On a scale of one to ten, PayPal scores ZERO for breaking every rule in the book when it comes to understanding security and how hackers go about their business. For such a large company, always being attacked, I would have thought that PayPal would have scored more than zero. It sent this email to me last night. Everything about the email is wrong, bad, stupid, and paves the way for hackers to have a field-day with PayPal customers.
See the email below. If we were to start with ten points, we would subtract 5 straight away for PayPal’s inclusion of a hyperlink in its email. First, never never never (to the power of 1000) NEVER send out an email to your clients and include a hyperlink in it. Because hackers and phishers and scammers will do the same, and say the same thing, and show the same hyperlink, except that they will trick users into clicking onto the hyperlink which will take them to another fake site that asks them to enter their details. This email from PayPal is asking customers to click on the link and enter their details: being the user name and password. This loses another 4 points. That’s nine down. The email should have simply said, go to your PayPal account and log in. It should NEVER have provided a link, because a phisher (a thief phishing/fishing for information about you) could have said and done the same thing, in EXACTLY the same way, except that the link would have gone to a fake site, asking people to log in, while stealing the user names and passwords. Wow, there you have it. What a simple way to gather user names and passwords. Now go shopping! Mind you, a client of mine alerted me to some fishy activity last year, so we wrote to PayPal, to do them a favour, and let me know about the fraud, and it was like talking to a brick wall. With evidence, an IP address, and hard-core information furnished to PayPal, they did not understand enough to know what we were talking about. And we were just trying to help them out. Our bad, as they say nowadays.
Furthermore, customers have been trained to believe that www.PayPal.com or www.PayPal.com.au are legitimate sites. However, look at who sent this note: It came from e.paypal.com.au. Who is ‘e’. This could be anyone. When and how were we told that ‘e’ is a legitimate address for PayPal? What if next week it says ‘s’ and so on? So how am I to know if this is real or not real? By training customers to accept emails from anything.paypal.com.au, PayPal is training its customers to not ask questions, and to surrender their vital details on a site. Which site? Look at the yellow highlighted box below. It shows that the innocent http://www.paypal.com.au does not go there at all. It goes to https://email-edg.paypal.com/r… etc. So in the future, a phisher can con customers by showing the same email, and having the link go to something random like secure-edg.paypalnet.com.
And who has signed this email? A complete no body. A faceless useless company with no names behind it. And what is the reply-to? Look at the ghastly reply-to. PayPal has no people to monitor emails. It says so. It says do not respond to us. This email is not monitored. Well dear people at PayPal, if you can send emails, but cannot receive emails, get out of cyberspace, and stay out! How disgraceful. That’s another 628 points lost, so really, this email shows that PayPal has no idea about security, about the risks, and about how phishers and hackers operate. If you do not know how they do it, you will not be able to protect yourself, so we can hold our breath and wait for another massive headline and a note from the CEO which would say, ‘Dear PayPal customer, sorry about the debacle last week, we are reviewing all our security protocol… and other such rubbish.’ Well Mr or Ms CEO, review them now before you end up on the front pages. But that might require some foresight.



Comments are closed.